Security researchers have discovered a powerful surveillance app first designed for Android devices can now target victims with iPhones.
The spy app, found by researchers at mobile security firm Lookout, said its developer abused their Apple-issued enterprise certificates to bypass the tech giant’s app store to infect unsuspecting victims.
The disguised carrier assistance app once installed can silently grab a victim’s contacts, audio recordings, photos, videos, and other device information — including their real-time location data. It can be remotely triggered to listen in on people’s conversations, the researchers found. Although there was no data to show who might have been targeted, the researchers noted that the malicious app was served from fake sites purporting to be cell carriers in Italy and Turkmenistan.
The app is one of several under the so-called “stalkerware” umbrella, apps that can be surreptitiously installed on a victim’s phone to spy on their activity, location and messages in real-time.
Researchers linked the app to the makers of a previously discovered Android app, developed by the same Italian surveillance app maker Connexxa.
The Android app, dubbed Exodus, ensnared hundreds of victims — either by installing it or having it installed. Exodus had a larger feature set and expanded spying capabilities by downloading an additional exploit designed to gain root access to the device, giving the app near complete access to a device’s data, including emails, cellular data, Wi-Fi passwords and more, according to Security Without Borders.
Screenshots of the ordinary-looking iPhone app, which was silently uploading a victim’s private data and real-time location to the spyware company’s servers. (Image: supplied)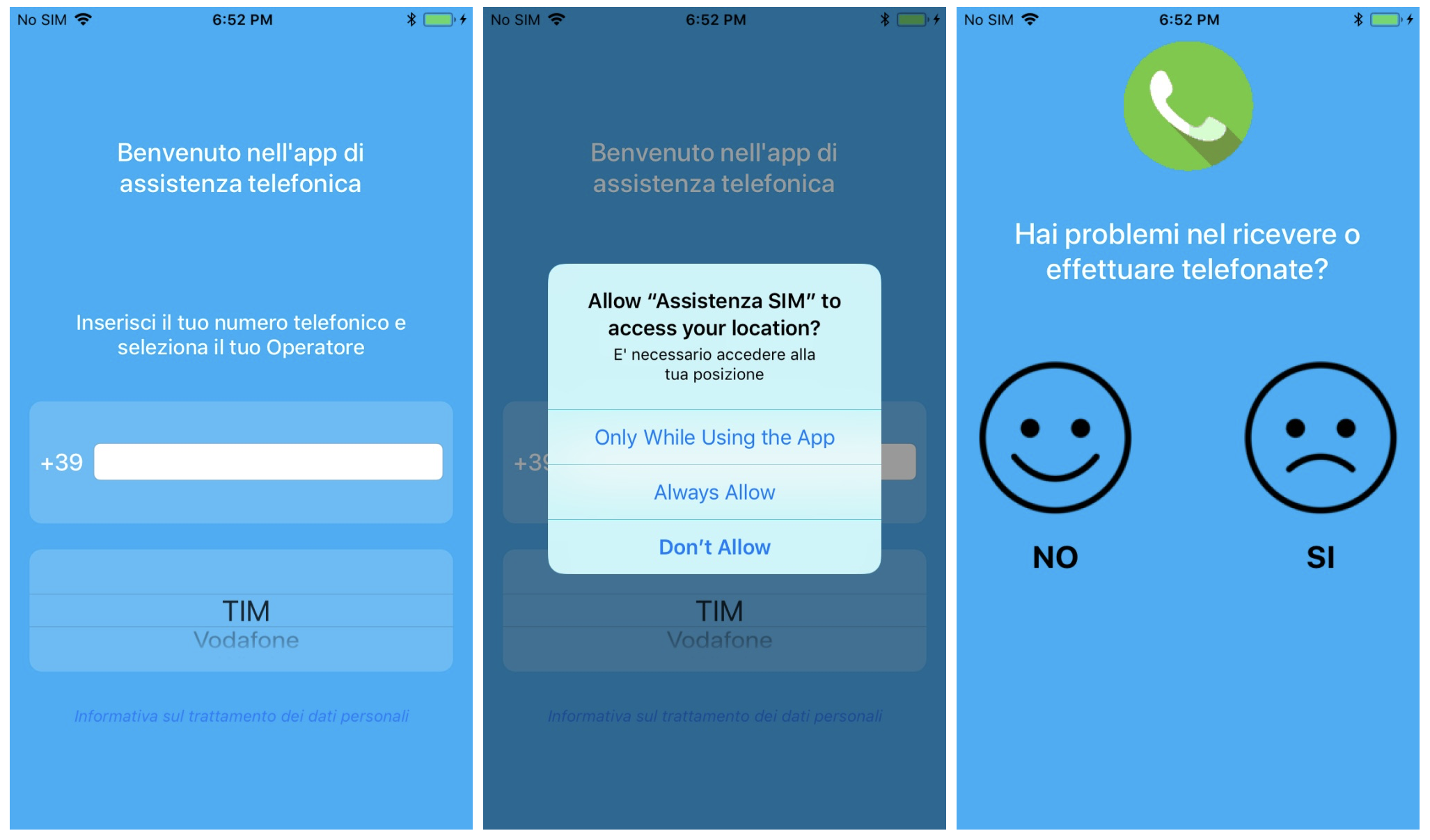
Both of the apps use the same backend infrastructure, while the iOS app used several techniques — like certificate pinning — to make it difficult to analyze the network traffic, Adam Bauer, Lookout’s senior staff security intelligence engineer, told TechCrunch.
“This is one of the indicators that a professional group was responsible for the software,” he said.
Although the Android version was downloadable directly from the Google’s app store, the iOS version was not widely distributed. Instead, Connexxa signed the app with an enterprise certificate issued by Apple to the developer, said Bauer, allowing the surveillance app maker to bypass Apple’s strict app store checks.
Apple says that’s a violation of its rules, which prohibits these certificates designed to be used strictly for internal apps to be pushed to consumers.
It follows a similar pattern to several app makers, as discovered by TechCrunch earlier this year, which abused their enterprise certificates to develop mobile apps that evaded the scrutiny of Apple’s app store. Every app served through an app store has to be certified by Apple or they won’t run. But several companies, like Facebook and Google, used their enterprise-only certificates to sign apps given to consumers. Apple said this violated its rules and banned the apps by revoking enterprise certificates used by Facebook and Google, knocking both of their illicit apps offline, but also every other internal app signed with the same certificate.
Facebook was unable to operate at full capacity for an entire working day until Apple issued a new certificate.
The certificate Apple issued to Connexa. (Image: supplied)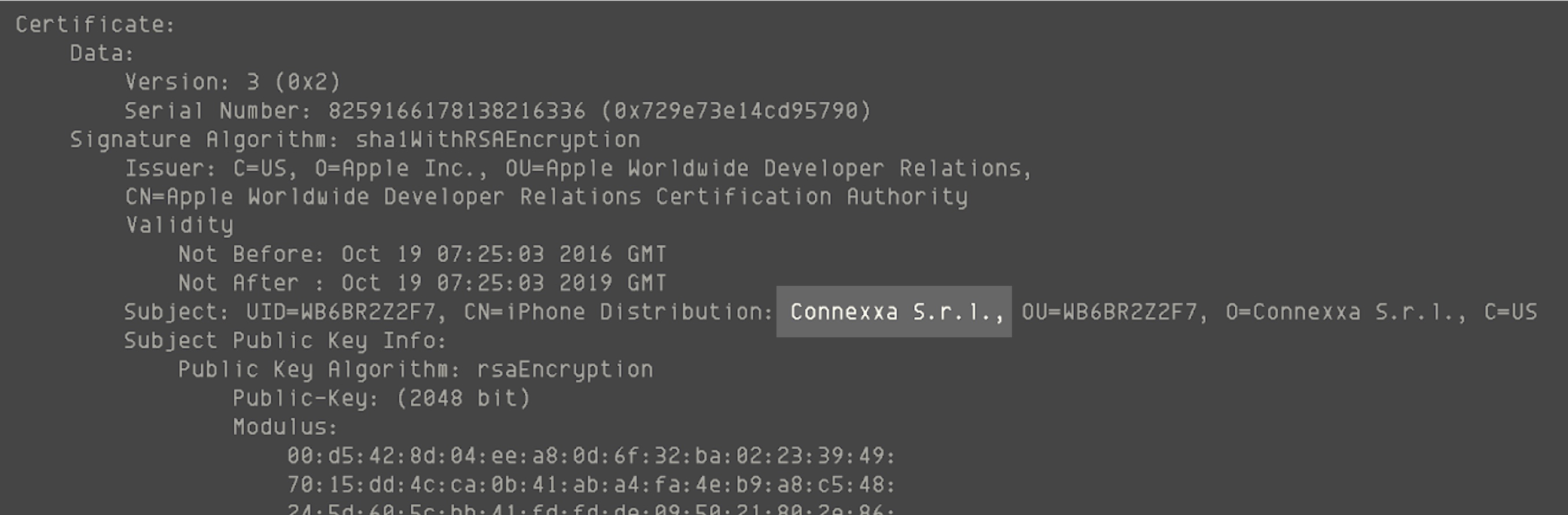
But Facebook and Google weren’t the only companies abusing their enterprise certificates. TechCrunch found dozens of porn and gambling apps — not permitted on Apple’s app store — signed with an enterprise certificate, circumventing the tech giant’s rules.
After they researchers disclosed their findings, Apple revoked the app maker’s enterprise certificate, knocking every installed app offline and unable to run.
The researchers said they did not know how many Apple users were affected.
Connexxa did not respond to a request for comment. Apple did not comment.
Researchers find a new malware-friendly hosting site after a spike in attacks
