Report details shifting ransomware ecosystem, U.S. election themed scams, and emergence of new AI tools for cybercrime
Trellix, the cybersecurity company delivering the future of extended detection and response (XDR), today announced The CyberThreat Report: June 2024, the latest report from the elite team of researchers with the Trellix Advanced Research Center. The report details increasing cyber activity tied to China- and Russia-linked threat actors, the emergence of U.S. election donation-themed phishing scams, an atypical ransomware ecosystem and the growing use of hard to detect threat actor tools designed to circumvent the endpoint detection and response (EDR) protection technologies used by organizations around the world.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20240611204272/en/
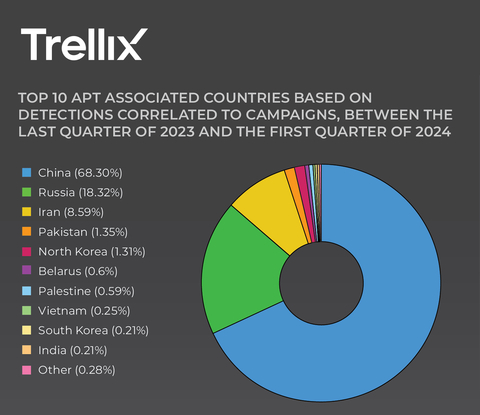
Trellix identifies the top 10 APT associated countries based on detections correlated to campaigns between the last quarter of 2023 and the first quarter of 2024. (Graphic: Business Wire)
“The last six months have been unprecedented - a state of polycrisis remains and everything from elections to warfare to law enforcement activity have accelerated cyber threat actor activity globally. We’re seeing radical shifts in behavior,” said John Fokker, Head of Threat Intelligence, Trellix. “The cat and mouse game of cybersecurity is becoming more complex. Security leaders need more operational threat intelligence in order to outpace cybercriminals.”
The Trellix Advanced Research Center’s latest CyberThreat Report details findings from October 2023 - March 2024. Highlights include:
- China and Russia increase attacks: China-linked threat groups, like Volt Typhoon, remain the most prolific originator of advanced persistent threat (APT) activities, generating 68.3% of all detections. The Trellix Advanced Research Center further found 23% of all activity from China-linked groups is directed at the global government sector. Additionally, Russia-linked APT group, Sandworm, saw a sharp increase in activity, with 40% more detections in the period of this report compared to April - September 2023.
- Election themed scams: The Trellix Advanced Research center found malicious emails aimed at tricking consumers into donating to elections. The emails abuse legitimate marketing services to create convincing but fake donation pages with the goal of scamming everyday people out of money disguised as donations to election campaigns.
- Shifting ransomware ecosystem: Ransomware actors threatened the transportation and shipping sector the most, generating 53% and 45% of global ransomware detections in Q4 2023 and Q1 2024 respectively, and was followed by the finance industry. Also, following a global law enforcement action to disrupt ransomware gang LockBit, Trellix observed imposters copying the group.
- EDR evasion: An EDR evasion tool called “Terminator” from cybercriminal developer Spyboy was used in a new campaign in January 2024 with 80% of detections targeted at the telecom sector. Given the specific targets, Trellix assesses with a high level of confidence that the campaign was related to the Russian-Ukrainian conflict.
- GenAI usage by cybercriminals: Trellix observed a free ChatGPT 4.0 Jabber tool available in the cybercriminal underground, which allows threat actors to adopt GenAI into their operations and to create a GenAI knowledge base to learn from other cyber criminals or even steal their ideas and tools.
New cyber actors emerge daily while new vulnerabilities, exploits, and tactics are constantly discovered. Operational threat intelligence, like the data and insights found in this report, is necessary for CISOs and security operations leaders looking for a comprehensive view into their security posture and to identify potential gaps in their cybersecurity strategy.
The CyberThreat Report: June 2024 includes proprietary data from Trellix’s sensor network, investigations into nation-state and cybercriminal activity by the Trellix Advanced Research Center, and open and closed-source intelligence. The report is based on telemetry related to detection of threats, when a file, URL, IP-address, suspicious email, network behavior, or other indicator is detected and reported by the AI-powered Trellix XDR platform.
Additional Resources:
- The CyberThreat Report: June 2024
- Trellix Advanced Research Center
- Trellix Advanced Research Center LinkedIn Newsletter
About the Trellix Advanced Research Center
The Trellix Advanced Research Center is at the forefront of research into the emerging methods, trends, and tools used by cyber threat actors across the global cyber threat landscape. Our elite team of researchers serve as the premier partner of CISOs, senior security leaders, and their security operations teams worldwide. The Trellix Advanced Research Center provides operational and strategic threat intelligence through cutting-edge content to security analysts, powers our industry leading AI powered XDR platform, and offers intelligence products and services to customers globally. More at https://www.trellix.com/en-us/advanced-research-center.html.
Follow Trellix on LinkedIn and X.
View source version on businesswire.com: https://www.businesswire.com/news/home/20240611204272/en/
Contacts
Media Contact
Sarah Erman
media@trellix.com




