Addressed new cyber vulnerability–named HTTP/2 Rapid Reset–alongside industry peers to make the Internet more secure for everyone
Cloudflare, Inc. (NYSE: NET), the leading connectivity cloud company, today made public that it helped lead the disclosure of a new novel zero-day vulnerability, dubbed “HTTP/2 Rapid Reset.” This global vulnerability gives attackers the ability to generate attacks larger than anything the Internet had seen before. To help mitigate the impact of this new threat for the entire Internet ecosystem, Cloudflare developed technology purpose-built to automatically block any attack leveraging Rapid Reset for its customers.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20231010515133/en/
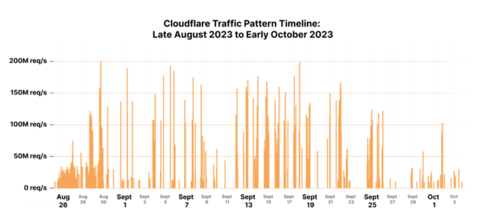
Cloudflare Traffic Pattern Timeline: Late August 2023-Early October 2023 (Graphic: Business Wire)
Cloudflare successfully mitigated these issues and halted potential abuse for all customers, while simultaneously kicking off a responsible disclosure process with two other major infrastructure providers, to extend mitigations for this vulnerability to a large percentage of the Internet prior to disclosing its existence to the general public.
“Successfully mitigating this threat for every critical infrastructure organization, customer, and the Internet at-large is the lifeblood of what Cloudflare stands for. We are one of the only companies equipped to identify and address threats of this magnitude, at the speed required to maintain the integrity of the Internet,” said Matthew Prince, CEO at Cloudflare. “And while this DDoS attack and vulnerability may be in a league of their own, there will always be other zero-day, evolving threat actor tactics, and new novel attacks and techniques—the continuous preparation and response to these is core to our mission to help build a better Internet.”
Deconstructing HTTP/2 Rapid Reset
In late August 2023, Cloudflare discovered a zero-day vulnerability, developed by an unknown threat actor. The vulnerability exploits the standard HTTP/2 protocol—a fundamental piece to how the Internet and most websites operate. HTTP/2 is responsible for how browsers interact with a website, allowing them to ‘request’ to view things like images and text quickly, and all at once no matter how complex the website. This new attack works by making hundreds of thousands of ‘requests’ and immediately canceling them. By automating this “request, cancel, request, cancel” pattern at scale, threat actors overwhelm websites and are able to knock anything that uses HTTP/2 offline.
“Rapid Reset” provides threat actors with a powerful new way to attack victims across the Internet at an order of magnitude larger than anything the Internet has seen before. HTTP/2 is the basis for about 60% of all web applications, and determines the speed and quality of how users see and interact with websites.
Based on Cloudflare's data, several attacks leveraging Rapid Reset were nearly three times larger than the largest DDoS attack in Internet history. At the peak of this DDoS campaign, Cloudflare recorded and handled over 201 million requests per second (Mrps), as well as the mitigation of thousands of additional attacks following.
How Cloudflare thwarted the attack with Industry peers
Threat actors who possess record-shattering attack methods have an extremely difficult time testing and understanding their effectiveness, due to the lack of infrastructure to absorb the attacks. For this reason, they often test against providers like Cloudflare to better understand how their attacks will perform.
“While large-scale attacks such as those leveraging vulnerabilities like Rapid Reset can be complex and difficult to mitigate, they provide us unprecedented visibility into new threat actor techniques early in development,” said Grant Bourzikas, CSO at Cloudflare. “While there is no such thing as ‘perfect disclosure,’ with downtime and bumps along the way, thwarting attacks and responding to breaking incidents requires organizations and security teams to live by the ‘assume breach’ mindset the Cloudflare team fosters. Ultimately, this allows us to be a proud partner that helps make the Internet secure.”
To learn more about HTTP/2 Rapid Reset and what Cloudflare has seen:
- Register for our upcoming webinar: HTTP/2 Rapid Reset DDoS Attack Campaign
- Visit our HTTP/2 Rapid Reset resources page
- Overview Blog: Exploit of Zero-Day HTTP 2.0 vulnerability results in record-breaking DDoS Attack
About Cloudflare
Cloudflare, Inc. (NYSE: NET) is the leading connectivity cloud company. It empowers organizations to make their employees, applications and networks faster and more secure everywhere, while reducing complexity and cost. Cloudflare’s connectivity cloud delivers the most full-featured, unified platform of cloud-native products and developer tools, so any organization can gain the control they need to work, develop, and accelerate their business.
Powered by one of the world’s largest and most interconnected networks, Cloudflare blocks billions of threats online for its customers every day. It is trusted by millions of organizations – from the largest brands to entrepreneurs and small businesses to nonprofits, humanitarian groups, and governments across the globe.
Learn more about Cloudflare’s connectivity cloud at cloudflare.com/connectivity-cloud. Learn more about the latest Internet trends and insights at https://radar.cloudflare.com.
Follow us: Blog | X | LinkedIn | Facebook | Instagram
Forward-Looking Statements
This press release contains forward-looking statements within the meaning of Section 27A of the Securities Act of 1933, as amended, and Section 21E of the Securities Exchange Act of 1934, as amended, which statements involve substantial risks and uncertainties. In some cases, you can identify forward-looking statements because they contain words such as “may,” “will,” “should,” “expect,” “explore,” “plan,” “anticipate,” “could,” “intend,” “target,” “project,” “contemplate,” “believe,” “estimate,” “predict,” “potential,” or “continue,” or the negative of these words, or other similar terms or expressions that concern Cloudflare’s expectations, strategy, plans, or intentions. However, not all forward-looking statements contain these identifying words. Forward-looking statements expressed or implied in this press release include, but are not limited to, statements regarding Cloudflare’s plans and objectives for its global network and its products and technology to block Internet attacks (including those leveraging HTTP/2 Rapid Reset), the effectiveness of Cloudflare’s products and technology to block Internet attacks (including those leveraging HTTP/2 Rapid Reset), Cloudflare’s technological development, future operations, growth, initiatives, and strategies, and comments made by Cloudflare’s CEO and co-founder, Matthew Prince, Cloudflare’s CSO, Grant Bourzikas, and others. Actual results could differ materially from those stated or implied in forward-looking statements due to a number of factors, including but not limited to, risks detailed in Cloudflare’s filings with the Securities and Exchange Commission (SEC), including Cloudflare’s Quarterly Report on Form 10-Q filed on August 3, 2023, as well as other filings that Cloudflare may make from time to time with the SEC.
The forward-looking statements made in this press release relate only to events as of the date on which the statements are made. Cloudflare undertakes no obligation to update any forward-looking statements made in this press release to reflect events or circumstances after the date of this press release or to reflect new information or the occurrence of unanticipated events, except as required by law. Cloudflare may not actually achieve the plans, intentions, or expectations disclosed in Cloudflare’s forward-looking statements, and you should not place undue reliance on Cloudflare’s forward-looking statements.
© 2023 Cloudflare, Inc. All rights reserved. Cloudflare, the Cloudflare logo, and other Cloudflare marks are trademarks and/or registered trademarks of Cloudflare, Inc. in the U.S. and other jurisdictions. All other marks and names referenced herein may be trademarks of their respective owners.
View source version on businesswire.com: https://www.businesswire.com/news/home/20231010515133/en/
Contacts
Cloudflare, Inc.
Daniella Vallurupalli
Vice President, Head of Global Communications
press@cloudflare.com





